Satya Nadella, Microsoft CEO, once said:
“Microsoft is the productivity and platform company for the mobile-first and cloud-first world. We will reinvent productivity to empower every person and every organization on the planet to do more and achieve more.“
Unfortunately, for many organizations, the cloud is still perceived as an unsafe platform.
In fact, according to a study we did with our users, 36% of the surveyed organizations listed “security concerns” as the top reason they weren’t migrating to the cloud.
Contrary to what people think, Office 365 has actually proven to be a very secure platform, when configured properly by the Administrators that is.
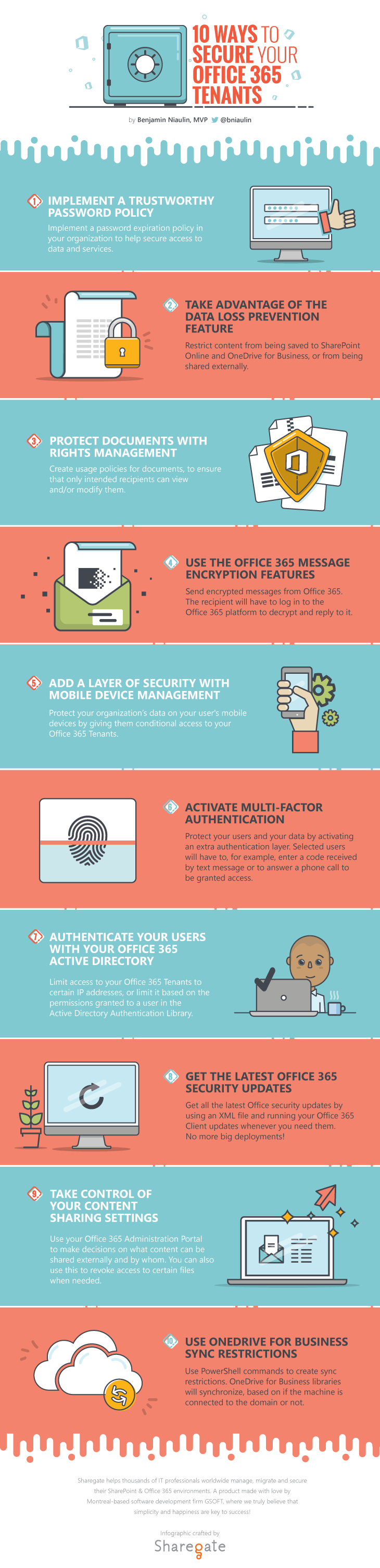
Inspired by Brian Reid’s 2015 Ignite Session, we decided to put together this handy infographic on 10 Ways to secure your Office 365 Tenants.
-
Implement a Trustworthy Password Policy
Too often we see Office 365 Tenants with account passwords without expiry dates, or passwords that aren’t secure enough.
What generally tends to happen is that users reuse the same passwords over and over. When asked to change it, they simply add a digit at the end of the previous one.
With this in mind, implementing an expiration policy in the organization can help secure the data and services access.
-
Take Advantage of the New Data Loss Prevention Feature
When users are added to an organization, it can become a real headache to ensure that data of a confidential or personal nature isn’t uploaded, shared, or emailed.
This headache can be avoided by creating policies to restrict certain types of content (credit card numbers for example) from being saved to SharePoint Online or OneDrive for Business, or shared externally.
It can also be done by creating document fingerprints to ensure standard company forms are not distributed.
Microsoft offers built-in Office 365 Reporting and Incident Management reports for IT Administrators to keep track and manage those policies.
-
Protect Documents with Rights Management
When looking into securing your Office 365 Tenant, it’s important to protect your sensitive data by encrypting documents with a usage policy, which will ensure they can only be seen and modified by the intended recipients.
An example of a usage policy, would be to give read-only access to a document, to a certain group of users. If the document is accidentally shared by email, it becomes impossible to open by anyone that isn’t in the group.
Microsoft makes it easy to protect your data by giving administrators the possibility of remotely revoking access to a file from the Rights Management Sharing Application.
-
Use the Office 365 Message Encryption Features
Using the Rights Management Sharing Application, Office 365 users can send encrypted messages requiring the recipient to log in to decrypt and reply to the message.
In this case, the recipient doesn’t directly receive a message, but a notification will be sent telling them that an encrypted message is waiting for them. The message will not leave the Office 365 platform.
Microsoft is also allowing users to use a one-time password (that will be sent by email) to avoid the need to log in.
-
Add a Layer of Security with Mobile Device Management
Because we live a mobile-centric era, users often need to access data on their devices while on the go. Microsoft know this and is helping organizations protect data on mobile devices using the Mobile Device Management feature.
Administrators can create device policies and register mobile devices as “Corporate compliant”, meaning users won’t be able to access corporate data before their device has been given conditional access.
This feature gives administrators access to reports on the state of these devices, as well as allowing them to easily remove corporate data if needed.
-
Activate Multi-Factor Authentication
The classic Username/Password credential authentication isn’t going anywhere, but now Office 365 offers up a way to add a second layer of security: Multi-Factor Authentication.
Once enabled, or “enforced” as it’s called in the Administration Portal, Office 365 will require that selected users comply with another “test” before logging in.
For example, an organization could require users to enter a code received by text message in order to complete the login process. Once this authentication is provided, open Sesame! They’re granted access to Office 365 in the most secure manner.
-
Authenticate Your Users with Your Office 365 Active Directory
Granting access to your Office 365 Tenant can be done with Active Directory, therefore familiar to many ITPros. However, it’s not because we are using the cloud, that we do not have the same security requirements at a network level.
With ADFS set up, you can create policies to limit access to Office 365 based on where the authenticated user is trying to access it from.
So if John, who usually only works from the office, is trying to access data from Singapore, you’ll be able to raise the alarm and block it.
-
Get the Latest Office 365 Security Updates
Microsoft never ceases to refine Office 365 security by releasing newly developed features and updates on a regular basis.
Using an XML file, you can select an update path, or simply run the default one, and update your Office 365 Client. You’ll get all the latest Office security updates, but you’ll also gain the flexibility of choosing which updates to install.
No more big deployments and you’ll always be up to date!
-
Take Control of Your Content Sharing Settings
Content is meant to be shared. But not all content should be shared with everyone!
In the Administration Portal, you can decide whether to allow external linking or not on a specific piece of content. This goes for your Sites, Skype for Business, Calendar, Third Party Apps, etc.
See who shared content from your Office 365 with whom on the outside of you organization, then remove their access as you will.
-
Use OneDrive for Business Sync Restrictions
Last but not least, the OneDrive for Business sync restrictions. This one will appear logical to many, while others may not be aware this is a thing.
By conducting a few PowerShell commands, you can determine on what machines your OneDrive for Business libraries will synchronize, based on whether they’re joined to your domain or not.
That way, a misplaced laptop won’t be the downfall of a highly secretive plan, if that’s what you’re into!